Central Git Repo With SSH
Note: This tutorial can be tried interactively on: https://katacoda.com/dashohoxha/courses/misc/central-git-repo-with-ssh
Introduction
To synchronize the work on a programming project we usually use GitHub, GitLab, etc. It is also possible to install and use one of the GitHub-like systems in your own server, like:
- https://gitea.io/
- https://about.gitlab.com/install/
- https://gitbucket.github.io/
- https://kallithea-scm.org/
- http://gitprep.yukikimoto.com/
- https://git.wiki.kernel.org/index.php/Gitweb
- http://gitblit.github.io/gitblit/
- https://gitlist.org/
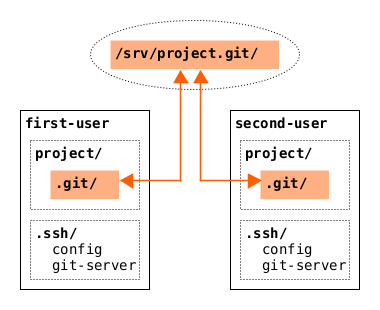
However if you don't need a web interface, issue management, pull requests, and other fancy features, you can easily create a central Git repository on your own server and access it through ssh. This tutorial shows how to do it.
Step 1 - Setup the central server
In this step we are going to setup the server. In the following steps we will do the setup for the first user and the second user.
Create user accounts. For each user that needs to access the central repo we will create an account on the server. Let's assume that we have two users and their accounts are named
user1anduser2.useradd -m -s /bin/bash user1 echo user1:pass1 | chpasswd useradd -m -s /bin/bash user2 echo user2:pass2 | chpasswd
Create a group for Git and add the users to this group:
addgroup git-group adduser user1 git-group adduser user2 git-group
Create a bare Git repository for the project:
git init --bare --shared /srv/project.git
Central Git repositories don't have a working tree. They are called "bare" repositories and are initialized with the option
--bare.The option
--sharedspecifies that this Git repository is to be shared amongst several users. This allows users belonging to the same group to push into this repository.Set the right group ownership to this repo:
chgrp -R git-group /srv/project.git chmod -R g+rw /srv/project.git chmod -R g+s /srv/project.git ls -al /srv/project.git
Notice the
setgidpermission that we set on the repo dir. Because of it, the new sub-directories or files that are created inside the repo dir will have the same group as the repo dir (git-group). This is convenient for a group of users that use the same directory.
Step 2 - First user setup
For the sake of example, the first user is named first-user. He
is going to use the account user1 on the server.
The following steps should be done on the computer of the first user.
Set up the ssh config for the central Git server:
mkdir ~/.ssh chmod 700 ~/.ssh/
SSH client configurations are usually kept on the directory
~/.ssh/, and it should be accessible only by the owner.cat <<EOF >> ~/.ssh/config Host git-server HostName host01 User user1 IdentityFile ~/.ssh/git-server IdentitiesOnly yes EOFIn this configuration entry we describe the details for the Host (server) named
git-server, which is an arbitrary name (we choose it). Its HostName in our example ishost01(which in our case resolves to the localhost, however usually it is a FQDN or an IP).The User account on the server
host01isuser1, and we will login there with an SSH key (IdentityFile) that is located on~/.ssh/git-server.The SSH key above doesn't exist yet, so let's create it:
ssh-keygen -t rsa -q -N '' -f ~/.ssh/git-server
The option
-N ''tells the command to use no passphrase for encrypting the private key, and-f ~/.ssh/git-servergives it the filename where the key should be saved.In order to be able to login to the server with this key, we need to send the public part of it to the server:
ssh-copy-id -i ~/.ssh/git-server.pub git-server
Now let's try to ssh to the server with the new key (should be able to do it without a password):
ssh git-server ls -al .ssh/ ssh git-server cat .ssh/authorized_keys
The command
ls -al .ssh/is running on the server, through ssh.Notice that the public key that we sent to the server has been appended to
.ssh/authorized_keyson the home directory ofuser1.Now that we configured an SSH connection to the server, let's create a test Git project (on the computer of
first-user):mkdir project cd project/ echo '# Test project' > README.md git init git add . git commit -m 'Initial commit'
Finally, let's set the remote and push this project to the server:
git remote add origin git-server:/srv/project.git git push --set-upstream origin master
Step 3 - Second user setup
The setup for the second user is similar to the first one. The following steps should be done on the computer of the second user.
Set up the ssh config for the central Git server:
mkdir ~/.ssh chmod 700 ~/.ssh/ cat <<EOF >> ~/.ssh/config Host git-server HostName host01 User user2 IdentityFile ~/.ssh/git-server IdentitiesOnly yes EOFCreate an SSH key with the filename (
~/.ssh/git-server) that we used above:ssh-keygen -t rsa -q -N '' -f ~/.ssh/git-server
Send the public key to the server:
ssh-copy-id -i ~/.ssh/git-server.pub git-server
Now try to ssh to the server with the new key (should be able to do it without a password):
ssh git-server ls -al .ssh/ ssh git-server cat .ssh/authorized_keys
Clone the Git project:
git clone git-server:/srv/project.git cd project/ git remote -v git log
This time we didn't have to add a remote, because the
originremote is added automatically when we clone the project.
Step 4 - Share Code
With this setup we can collaborate and share code by using the central Git repo as a coordinator.
Make some changes to the project, then commit and push it:
cat << EOF >> README.md First line EOF git add . git commit -m 'Update README' git push
Now switch to the first user and pull these changes:
cd ~/project/ git pull cat README.md git log